Introduction
User Guide
Administration Guide
- Lifecycle Management CLI
- Creating an Environment
- Restoring from Backup
- Deleting an Environment
- Monitoring
- Managing Blacklist/Whitelist
- Audit Logging
Authentication
Architecture
- Infrastructure Overview
- REST API
- High Availability
- Security Features
- Files in S3
- Alternative Solutions
Contributing
Quick Start
This is a quick start guide for application developers who want to use the Cerberus service. This guide assumes a Cerberus environment has been setup as described in the Administration guide.
Cerberus is a complete solution to manage anything that you want to tightly control access to, such as API keys, passwords, certificates, etc. By the end of this document you will be able to provision a safe deposit box (SDB), set the correct permissions, and integrate a cerberus client library to access data from your application. A safe deposit box (SDB) is a logical grouping of data with a single set of access controls.
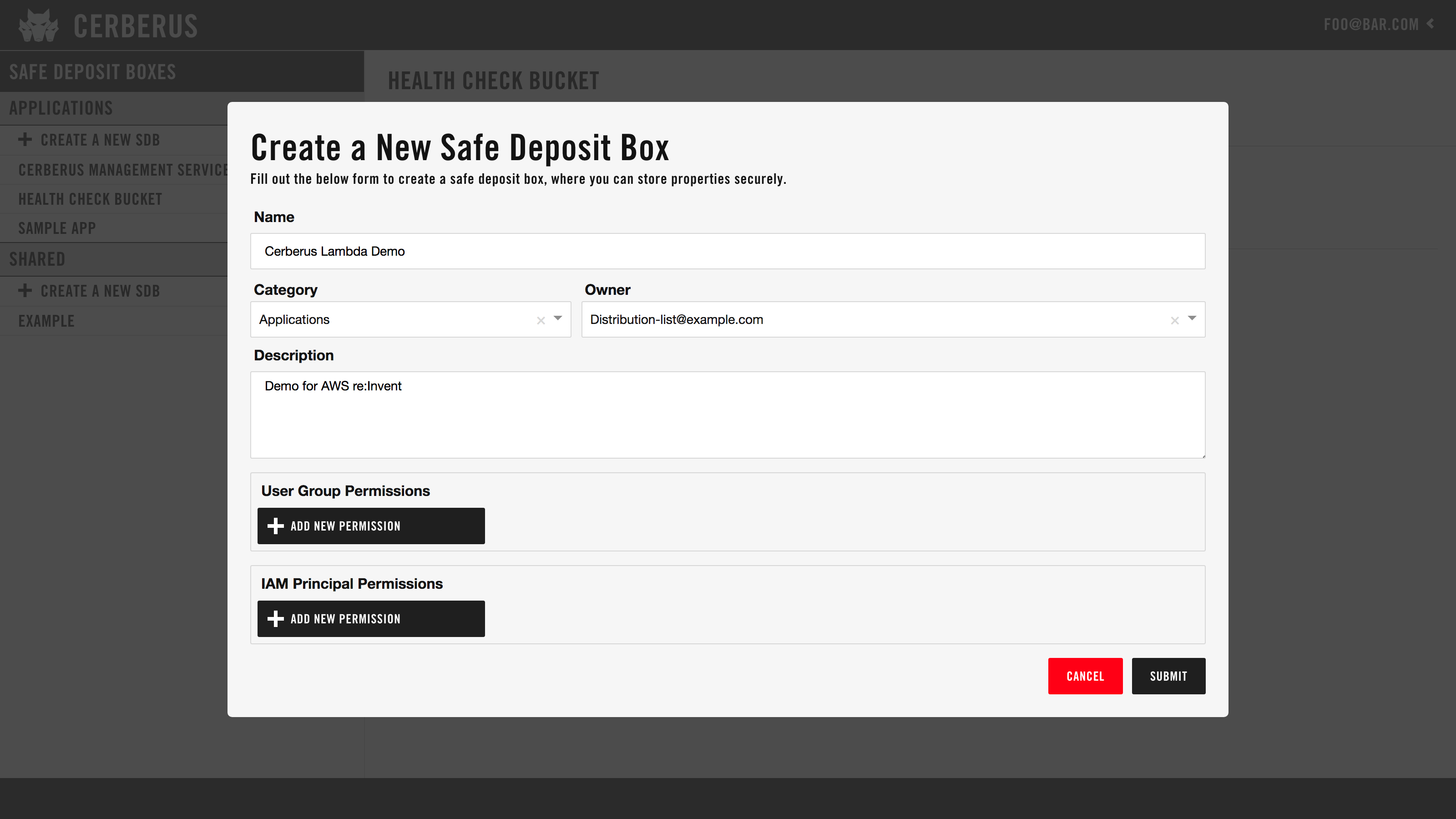
1. Create a Safe Deposit Box
- Login to the Cerberus dashboard with your credentials.
- In the left navigation bar, click the “+ Create a New SDB” button next to the Applications section.
- Enter a descriptive name for your SDB. If your app is “myexampleapp”, use “My Example App”.
- The owner field is the Active Directory group that will have ownership and admin privileges for this SDB. Select one of the AD groups of which you are currently a member.
- Under “User Group Permissions”, you can give additional Active Directory groups, that you are a member of, read or write access to the SDB. This is optional.
- Under “IAM Principal Permissions”, you can provide the AWS role name that will have either read or write access to the SDB. This is optional. See “How to add an IAM Principal Permission” section below.
- Click the “SUBMIT” button.
How to add an IAM Principal Permission:
- Under “IAM Principal Permissions”, click the “+ Add New Permission” button.
- Construct an IAM Principal ARN. See the example below. In this example, “1111111111111” is the account ID. The account ID in the ARN should be the account ID for the user’s account. See your company’s internal documentation for the account ID that you should use. “ExampleAdminRole” is the base role. Please note that because Cerberus uses STS Auth, this IAM Principal ARN does NOT contain paths.
arn:aws:iam::1111111111111:role/ExampleAdminRole - Select whether you want read or write permissions for this ARN.
- Click “SUBMIT”.
- See AWS STS Authentication for more information.
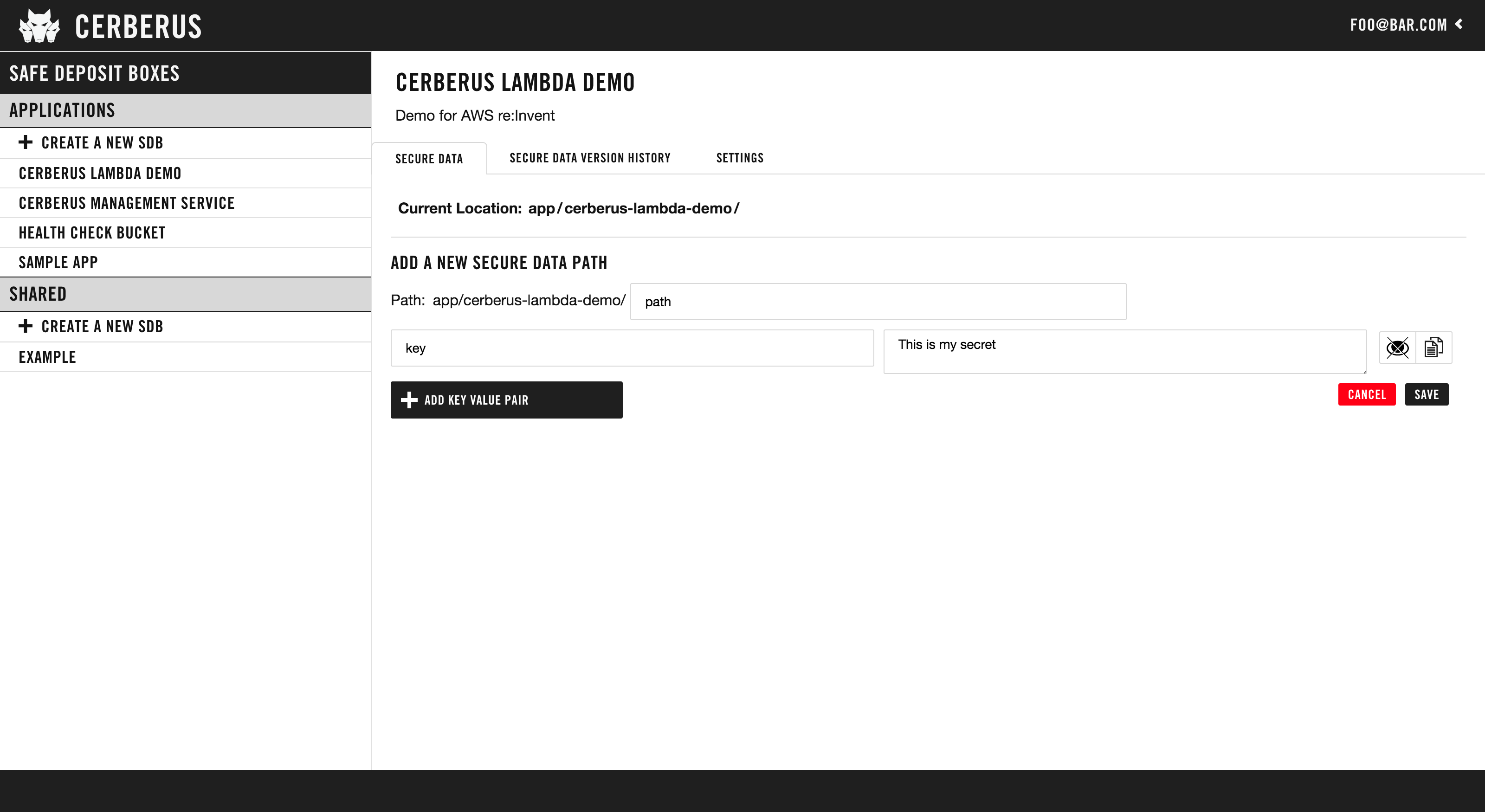
2. Manage Data in your Safe Deposit Box
Data is stored using a path structure. Note that the application name is normalized to be URL friendly. So, if you had “My Example App” in the Applications category your root path will be “applications/my-example-app”. From there you can add sub-paths to store key value pairs.
Cerberus will allow an SDB to contain a folder structure with many subpaths. However for most applications, a single path with a list of several key/value pairs is optimal. This allows all values to be read with a single API call.
How to add a subpath:
- Click the “Add new path” button.
- Enter a subpath name.
- Add the key/value pairs that you’d like to store at that subpath.
- Click “SAVE”.
- The page will refresh and you’ll be able to add more subpaths or edit the subpath you just added.
3. Access Your Secrets with Cerberus
Use one of the Cerberus Clients. The clients are also listed below:
Don’t see your desired client? Cerberus has a REST API. You can contribute a new client or use the REST API directly.
Local Development
To get started with local development, check out the Cerberus README.
Verifying Your Identity
A common problem encountered during setup is using a different role to authenticate than the one you expect.
See Who am I? for more information on how to verify your identity.